Development of a wireless sensor network protocol based on a data-oriented architecture
Agenda
- Ⅰ. Introduction
- Ⅱ. Related Work
- Ⅲ. Research and Development Items
- Ⅲ.A. Development of an efficient caching scheme for WSNs based on ICN
- Ⅲ.B. Cross-layer optimization and computer-simulation evaluation
- Ⅲ.C. Development of a secure cashing scheme using blockchain and its initial evaluation
- Ⅳ. Development of Efficient Caching Scheme for ICN-based WSNs
- Ⅳ.A. Literature review regarding efficient caching scheme
- Ⅳ.B. Network model
- Ⅳ.C. Key concept of the proposed scheme
- Ⅳ.D. SIC-based cashing scheme
- Ⅴ. Cross-Layer Design-based Optimization
- Ⅴ.A. Protocol stack of the proposed scheme
- Ⅴ.B. Procedure of the cross-layer-design signal processing
- Ⅴ.C. Simulation model (wireless propagation model)
- Ⅴ.D. Computer simulation
- Ⅵ. Development of Secure Caching Scheme using Blockchain
- Ⅵ.A. Literature review regarding blockchain
- Ⅵ.B. Overview of the proposed secure caching scheme
- Ⅵ.C. Secure sensing data collection methods
- Ⅵ.D. Blockchain-based data management
- Ⅵ.E. Numerical examples of hash function
- Ⅵ.F. Conditions under which the development system works
- Ⅵ.G. Computer simulation
- Ⅶ. Conclusion
- Acknowledgement
- Outcomes
Ⅰ. Introduction
A few years later, wireless communication services based on 5G will be provided, and wireless sensor networks based on the Internet of Things (IoT)/machine-to-machine (M2M) will be widely deployed in our daily lives. As we can see in current daily life, people's interests are concentrated on common services such as Google, Facebook, and Amazon when they access the Internet via mobile devices, such as smartphones. In other words, it is a paradigm shift from “end-to-end” to “content.” In the near future, wireless network systems should not be designed based on conventional IP networking but on content-oriented architecture, which is the next generation of Internet architecture.
In modern society, IoT (connecting various things to the Internet) is a major paradigm shift, expanding people-to-people communications to M2M. In addition, there are many scenarios for monitoring using wireless sensor networks with large numbers of sensor nodes, such as Infrastructure maintenance, disaster and disaster prevention management, and observation of agricultural, forestry, and fishery resources. In this situation, one important issue is establishing a method for efficiently transmitting vast amounts of data wirelessly.
From a technological perspective, the IP networks underpinning existing wired and wireless communication networks are well-established. However, this is not adequate if it is applied to the telecommunications infrastructure for a future advanced information society. There should be serious consideration when introducing new architecture. In recent years, in the field of wired network research, in place of host-oriented networks based on IP, widely used on the Internet and other networks, alternative network systems based on information-centric networking (ICN) paid attention, which is designed based on the data to be sent and received.
This study was inspired by the development of a new protocol design based on ICN for the application of WSN in biological communications. Although the design and effectiveness of the proposed approach were recognized as innovative and promising, there were still many unsolved issues in terms of effectiveness and reliability. If we introduce ICN into WSN, it is necessary to investigate the naming policy, name resolution, routing, caching, mobility, and security. In particular, we found that the caching method was an important element of these technologies, and we, therefore, recognized the necessity of theoretical protocol design and fundamental evaluation based on computer simulations, which will provide essential knowledge for constructing a new WSN infrastructure.
Ⅱ. Related Work
The paradigm of the modern Internet shifts from “Which device to access data from?” to “What content to access?” In the future Internet architecture, ICN architecture will inevitably become popular. As mobile internet access via smartphones and tablet PCs becomes more common, the issues related to Internet technology should be discussed not only in terms of wired communication but also in terms of wireless communication. In particular, for 5G and After/Post/Beyond 5G, there are strong demands for its introduction to WSNs based on IoT/M2M. In some proposals of mobile networks, popular content that users desire is copied to base stations using content delivery network (CDN) technology, and core networks are designed based on ICN technology.
Here is an overview of the caching method, which is an important elemental technology in this study. In typical ICN platforms, data-oriented network architecture (DONA), content-centric networking (CCN), and named data networking (NDN) only support the on-path caching method. On the other hand, a new message protocol has been introduced to support the off-path cashing scheme, and the hash-chain technology has been used to reduce the overhead of introducing the scheme. In both cases, it is only just starting with research and development of the elemental technologies for ICN architecture for IoT/M2M. In addition, as for cashing methods, they either target wired communication or introduce technologies developed for wired communication to wireless communication.
Ⅲ. Research and Development Items
Ⅲ.A. Development of an efficient caching scheme for WSNs based on ICN
This study aims to introduce an ICN architecture into WSN systems, not wired network systems. In the caching method in ICN, the system should establish a link between the node that requests the contents and the node that has them. Here, there are two types of caching methods: on-path caching, where the relays on the route hold the cached data, and off-path caching, where other nodes store the data on their local storage. In general, in wireless communication, the nodes near the transmitting and receiving nodes have specific characteristics, which can be obtained overheard by communication via radio signals. In this study, we develop a novel scheme for off-path caching in WSNs based on the feature of overhearing. Fundamentally, ICN architecture has been designed for wired communication systems, and off-path caching techniques have not been introduced or have been implemented using separate channels. In addition, the proposed scheme has the advantage of off-path caching without overhead and without introducing any new complicated mechanisms.
Ⅲ.B. Cross-layer optimization and computer-simulation evaluation
In order to effectively transfer caching data from the sensor node, we will develop a new wireless communication technology using the successive interference cancellation (SIC) technique. The SIC technique has been developed as an elemental technology for the cellular-network field. It has been implemented and commercialized as an LSI chip for a next-generation high-speed mobile communication system. In the SIC technique procedure, the received signal is restored according to the strongest signal strength. If the decoding is successful, the decoded data is re-encoded and then subtracted from the received signal. Through repeating this operation, the strongest interference can be removed, which helps to improve the probability of successful decoding. In contrast, the concept of the SIC technique has not been considered in the network field, and this study emphasizes this factor as a novelty.
Ⅲ.C. Development of a secure cashing scheme using blockchain and its initial evaluation
Here, we conduct theoretical analysis using a statistical model, assuming it is used in WSNs. In addition, we will discuss the feasibility of protocol design with researchers in both the wired and wireless network fields. ICN architecture is relatively innovative, and it is difficult to evaluate using hardware-based experiments. Therefore, for the evaluation of the proposed scheme, we will use not only theoretical calculations but also computer simulations. Note that in this evaluation, we implement the simulator using C++. At the same time, we have recognized the necessity of a mechanism for secure sensing-data sharing within the WSN system, prior to evaluation based on testbeds. Therefore, to establish this mechanism, we introduce blockchain technology and adopt it into the development system. In particular, it is necessary to achieve a distributed data management approach that differs from conventional host-oriented networks, such as IP networks, and blockchain has significant suitability for WSNs based on ICN.
Ⅳ. Development of Efficient Caching Scheme for ICN-based WSNs




Ⅳ.A. Literature review regarding efficient caching scheme
In the wired network field, ICN technology is attracting attention as a next-generation Internet architecture, gradually spreading to wireless networks. For example, some proposals have been investigated in cellular networks, such as caching in base stations, gateways, and routers. In other words, it enables the reduction of backhaul network traffic thanks to the distribution of the same data. In this situation, ICN is similar to CDN, but the difference is that CDN caches contents within the network server, whereas ICN stores contents widely in the terminal nodes.
Based on an analysis of a large number of ICN-related studies, the cashing method was classified into two types: on-path cashing and off-path cashing. Namely, on-path caching stores content in the relay nodes on the route, whereas off-path caching actively copies content to nodes outside the route. In a typical ICN framework, on-path caching is provided as standard in DONA and NDN. There are four off-path caching methods: user cooperative caching methods, data selection methods, and dynamic caching methods for video streaming delivery with guaranteed quality of service (QoS).
Ⅳ.B. Network model
In ICN-based WSNs, the content data are stored in SNs. Similar to CDNs, ICNs do not distinguish between original data and copied data. As shown in Fig. 1, in the proposed scheme, the sensing data are stored in the cache memory in the SN as cached content data. Regarding the procedure for retrieving any sensing data, in typical WSNs, the SN connects to the cloud server via the Internet, where the sensing data is centrally managed. Therefore, the user who desires to obtain sensing data only needs to access the cloud server. On the other hand, in the proposed scheme, the user accesses the gateway node that belongs to the WSN because it is necessary to find the relevant sensing data from the content data stored in the network. The gateway node, acting as a subscriber, broadcasts a request to acquire sensing data within the network and launches a procedure to conduct the investigation. When the sensor node that holds the desired sensing data from the user responds to the previous request and transmits the relevant sensing data, it completes the task.
As a mechanism to enable routing data from the publisher to the subscriber, the proposed scheme makes it possible by recording the tracking information of the request packet sequentially when it is flooding. In addition, since the tracking information is contained in the header of the request packet, it is possible to distinguish among each request, and it is also possible to identify the next destination (sender) to be sent.
Ⅳ.C. Key concept of the proposed scheme
As shown in Figure 2, the proposed scheme uses both on-path and off-path caching. Regarding on-path caching, the scheme is implemented in the same manner as other studies, where sensing data are forwarded from the publisher to the subscriber in the response process, and the relay node stores the sensing data in its own cache memory. On the other hand, in the case of off-path cashing, based on the overhearing phenomenon, the relay node accumulates the overheard sensing data, which is sent from the SNs that are in the relay node’s communication coverage area.
Due to the overhearing phenomenon, the proposed scheme does not require any unnecessary wireless communication between the relay node and the adjacent sensor node. In contrast, to perform overhearing-based communication, it is necessary to consume more power for radio signal processing and further increase the cache memory capacity. Even if the energy consumption of the microcontroller and other processing in the SN increases, the total energy consumption of the SN can be improved by reducing the number of wireless communications by introducing the proposed scheme because the energy consumption of the wireless communications is smaller than that of the calculations. In addition, the cost of extra cache memory is more than paid for by the savings in radio frequency resources, which can reduce the number of wireless communications. However, since the capacity of the cache memory in the SN is not unlimited, the rules for discarding sensing data stored in the cache memory must be decided according to the environment in which the proposed method is adopted. This question is not covered in this paper, and the detailed decision-making process is a future work.
Ⅳ.D. SIC-based cashing scheme
SN can receive signals from adjacent SNs based on the overhearing phenomenon, and it can be used positively on the basis of the aforementioned method, but it can also be a double-edged sword that causes interference that reduces the data reception probability. Therefore, we use the SIC technique to reduce interference from other SNs in off-path caching based on the received signal. As shown in Fig. 3, let , denote the signal strength transmitted from the -th SN to the -th SN, the set of SNs that the -th node can receive based on the overhearing phenomenon. Letting denotes the desired signal, in general, conditions under which the receiver can decode is given by
where is a threshold value that can be successfully decoded, is an ambient noise, respectively.
In Fig. 3, denotes the -th SN’s received signal, which is given by
Figure 4 shows the procedure of the proposed decoder. In the first decoding process, the signal with the strongest received signal is decoded. When the signal can be decoded correctly, the restored signal is encoded again, and the signal is subtracted from the received signal. In the same manner, it is repeated until no more signals can be decoded.
Ⅴ. Cross-Layer Design-based Optimization






Ⅴ.A. Protocol stack of the proposed scheme
For an ICN-based WSN system, in the case of introducing the overhearing phenomenon and caching method based on the SIC technique, the protocol design should be flexible and integrated. A cross-layer design-based approach is often suggested for optimizing the protocol stack. Cross-layer design is a technique that achieves a flexible layer design by sharing information between layers, unlike conventional layer designs (such as the OSI reference model). In particular, the design concept is based on the interconnection between adjacent layers and the protocol stack, as shown in Fig. 5. In the proposed scheme, the TCP/UDP, IP, and MAC layers of the conventional architecture are redefined as the ICN layer. The ICN layer is then divided into two types of control and data transmission functions, called the C-plane and U-plane, to achieve each function.
Ⅴ.B. Procedure of the cross-layer-design signal processing
Figure 6 shows the signal processing procedure for cross-layer design in the proposed scheme. The sensing data acquired from the observation area are stored in its own cache memory. As well as storing its sensing data, the cache memory also stores as much as possible in other SNs that it has overheard. The TX/RX RF (radio frequency) module sends and receives sensing data. On the other hand, the microcontroller not only manages the sensing data and routing table but also controls the cache memory and RF module. At this time, the signal transmission required for this control is designed according to a cross-layer design based on side information from the upper layer to the lower layer.
Figure 7 shows the detailed signal processing procedure in the RF module and wireless communication channel emulator, as shown in Fig. 6. As shown in Fig. 7(a), the transmission packet is encoded with a cyclic redundancy check (CRC) for error detection, and then each bit is modulated using the binary phase shift keying (BPSK) method. On the other hand, as shown in Fig. 7(c), the receiver performs soft decoding and then applies SIC technology using the decoded replica. The decoder and encoder in Fig. 7(c) are the same as the blocks shown in Fig. 4, and they perform packet restoration and signal subtraction processing according to the procedure described above.
Ⅴ.C. Simulation model (wireless propagation model)
As shown in Fig. 7(b), the packet error probability is calculated based on the received signal strength indicator (RSSI). In general, the link budget can be expressed by
where letting and denote the transmitter and receiver power, letting and denote antenna gain in TX and RX, and and denote the attenuation in the TX and RX electronic circuits, respectively.
In the above equation, is the path loss of the wireless channel. The packet error probability required for computer simulations is calculated based on the signal-to-noise ratio (SNR) and bit error probability. Specifically, the received SN signal power, and the SNR , is given by
where (= W/Hz)is Boltzmann’s constant, is the system temperature of the hardware device. We can theoretically calculate the bit error probability of BPSK under Rayleigh fading channel.
Ⅴ.D. Computer simulation
A computer simulator was implemented using the C++ language for the RF module, radio propagation model, and cache memory, as shown in Figs. 6 and 7. As a simulation scenario, SNs were randomly deployed in the observation field (i.e., the positions of the SNs were determined based on random uniform distribution). In this case, the combination of publisher and subscriber was randomly determined, and the shortest path was selected between the two nodes. In the simulator, the routing path was calculated based on the Dijkstra algorithm. The constant parameter settings of the RF device were determined based on the XBee module, which is widely used in wireless communication in WSNs.
Figure 8 shows the percentage of successful caching for all SNs . In accordance with the effect of the overhearing phenomenon, increases as the number of SNs increases, but decreases after reaching a maximum of 180 SNs. In comparison with the method that does not use the proposed cashing mechanism, the number of SNs was improved by 1.42 times, 2.61 times, 8.85 times, and 17.0 times when the number of SNs was 100, 180, 600, and 1,000, respectively.
Figure 9 shows the average number of multi-hops when the request packet is correctly transmitted from the publisher to the subscriber. As the number of SNs increases, the number of relay nodes that can forward packets also increases; thus, the average number of hops also increases. The proposed scheme uses significantly more cached data than the comparison scheme (Fig. 8), and the probability of a request packet hitting a cache is also higher, improving the average number of multi-hops. When the number of SNs was 50, 100, 150, and 200, we obtained improvements of 3.35%, 8.51%, 10.8%, and 10.9%, respectively.
Figure 10 shows the average transmission distance versus the number of SNs for the transmission link between the publisher and the subscriber. In the region where the number of SNs is less than 100, the proposed scheme is not effective because of insufficient caching, but in other regions, the performance is improved. Specifically, the system can improve by 6.46%, 10.5%, 12.3%, and 12.2% for the case number of SN are 50, 100, 150, and 200, respectively.
Ⅵ. Development of Secure Caching Scheme using Blockchain





Ⅵ.A. Literature review regarding blockchain
The security and attack protection framework in NDN has been designed and optimized to provide a secure method of data processing against caching in ICN. In addition, an approach to preventing attacks aimed at cache pollution in the NDN has been developed, and an analytical model of attack scenarios against the NDN has been constructed. Additionally, a secure approach to personal information in-home network systems has been proposed. Furthermore, the research trends in the IoT field that consider blockchain are explored.
Ⅵ.B. Overview of the proposed secure caching scheme
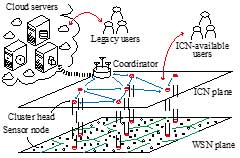
Implementing blockchain technology requires vast computational resources for authentication in the mining process. Therefore, it is difficult to apply the blockchain as it is to SN devices with poor hardware resources. As shown in Fig. 11, SN, cluster head (CH), and coordinator were classified based on hardware limitations, based on a two-level hierarchical model that we call ICN-plane and WSN-plane.
For the network structure in this study, SNs are grouped into several clusters, and CHs are assigned to each cluster. The CH consolidates the sensing data collected from SNs belonging to the dominant cluster and aggregates them to the cloud via the coordinator. At the same time, the CHs and coordinators that comprise the ICN plane also provide information based on the ICN. Here, we assumed that SN had sufficient hardware resources, but in reality, such an environment is uncommon.
Ⅵ.C. Secure sensing data collection methods
Before collecting sensing data, the CH generates a pair of public and private keys based on a public-key cryptographic algorithm. We consider CHs and the set of SNs belonging to the -th cluster. The CH assigned to the -th cluster generates a pair of public and private keys for the -th SN in the -th cluster. The private key generated here is shared between CH and SN, and the public key is stored in CH. According to the same procedure, a public/private key pair is exchanged between the CH and the coordinator. In other words, the coordinator generates public and private keys. In stage① of Figure 12, the SN generates the sensing data and signs a digital signature.
The sensing data with digital signatures is wirelessly transmitted to the CH assigned to the cluster to which it belongs. On the other hand, the SNs collected from the SNs are authenticated using a public key. In other words, the CH can know whether the generated SN is correct and has not been tampered with during transmission.
The recovered sensing data is stored in the buffer memory of the CH, and the sensing data is summarized as aggregated sensing data (summarized sensing data). The aggregated sensing data corresponds to the section of data that is addressed by the blockchain. Therefore, the aggregate sensing data is broadcast to the nodes that comprise the ICN-plane in stage ② of Fig. 12. The digital signatures are also assigned to aggregated sensing data to ensure a means of verifying the validity of the data to be distributed.
Ⅵ.D. Blockchain-based data management
In Fig. 13, the blockchain of the proposed scheme, each block consists of the hash value from the previous block, the aggregate sensing data, the nance, and the hash value to the current block. To append the aggregated sensing data to the blockchain, we should conduct the mining-based hash calculation. For this purpose, in stage ③ of Fig. 12, the coordinator sends a request to the CH for the mining operation.
Ⅵ.E. Numerical examples of hash function
In order to estimate the difficulty parameter for calculating the hash value, we conducted actual measurements using a Raspberry Pi 3 (Raspbian kernel ver. 4.9). The simulator was implemented using C++ language for MD5 (message digest algorithm 5) and SHA-1 (first-generation secured hash algorithm) hash functions. The CLX C++ library was used to implement the hash function, and the C++ standard library (std::chorono) was used to measure the processing time, which were compiled using the g++ compiler ver. 6.3.0. Figure 14 shows the average processing time for 100 trials for the parameter . According to the experimental results, when the block length is set to 100 kbyte, 500 kbyte, or 1 Mbyte, and when the mining time is assumed to be 1 or 10 minutes, it is sufficient to determine according to Fig. 14.
Ⅵ.F. Conditions under which the development system works
According to the Poisson distribution that aggregate sensing data are generated according to, the mean value of , which is given by
where is the number of clusters, is the number of summarized sensing data, is the average number of SNs per cluster, and is the number of sensing data per SN generated per unit time. When the summarized sensing data is verified by mining according to a Poisson distribution, the mean value of can be calculated based on
Due to the blockchain mechanism, even if a block is verified, it cannot be trusted unless several more blocks are linked after it. Let denotes the number of blocks connected after the verified block, denotes the validation time per transaction. For example, in Bitcoin, is set as 6 and as approx. 10 minutes. In this case, the proposed scheme can work under
Ⅵ.G. Computer simulation
On the basis of the aforementioned statistical model, we evaluate the effectiveness of the proposed scheme in terms of response time for sensing data retrieval in the case where the scheme is implemented into WSNs under low-power wide area networks (LPWANs) using computer simulations. The emulation of the wireless communication channel is calculated using the model described above.
Figure 15 shows the number of aggregated sensing data generated per unit time for the number of sensor nodes. When the number of SNs was less than 75,000, , , and are constants and is continuously increased, but when the number of SNs was more than 75,000, becase of the MAC protocol used the pure ALOHA method, it degraded the characteristics due to collisions. That is, reached the maximum value when the number of SNs was 88.4. According to the equality condition, if is 88.4, the desired is 88.4. Therefore, the maximum verification time is 40.7 seconds per block. Therefore, on the basis of Figure 14, in the case of using the MD5 and SHA-1 algorithms can be determined to be 14 and 15, respectively.
To evaluate the effectiveness of the proposed scheme, the response time between the request for sensing data and its delivery was calculated as a benchmark. Figure 16 shows the ratio of the total number of sensor nodes to the number of sensor nodes that have the desired sensing data stored in cache memory, i.e., the response time versus cache hit probability . As a result, the response time is an average of 10, 000 trials. When the proposed scheme worked under the best conditions (i.e., was 1), the response time was 0 seconds because all SNs have all caching data because the subscriber and the publisher were the same. On the other hand, when the development system worked under the worst conditions (i.e., was 0), the average response time was 176 seconds. Note that the worst case equates to the conditions under which the proposed scheme is ineffective. As a result, when was 0.2, 0.5, and 0.7, the proposed scheme can improve by 36.1%, 75.1%, and 95.9%, respectively.
Ⅶ. Conclusion
In this study, we proposed and evaluated an effective caching scheme for introducing ICN into WSNs. Specifically, we developed a technique that combined SIC technology with off-path caching based on the overhearing phenomenon. For the signal process, we optimized the procedure based on a cross-layer design. In addition, the effectiveness of the proposed scheme was evaluated by computer simulations.
Prior to the demonstration in a realistic environment, we preliminary evaluated the secure mechanism. We developed a management methodology for caching data based on a distributed blockchain-based ledger. In addition, we developed a test bed and demonstrated the effectiveness of the scheme based on computer simulations. The purpose of this study has been achieved, but we should consider the development and evaluation of the practical test bed, which is future work.
The main objective of this study is to develop elemental technology for ICN-based WSNs. However, further development must consider mobility and security. Since terminal nodes are assumed to be mobile and radio waves propagate in free space, security should be considered an essential issue.
Acknowledgement
A part of this work is supported by the TAF (Telecommunications Advancement Foundation).
Outcomes
- Shintaro Mori, “A study on off-path caching scheme by using successive interference cancellation for information-centric network-based wireless sensor network,” Proc. IARIA the 16th International Conference on Networks (ICN 2017), pp. 42–45, Venice, Italy, Apr. 2017. (ThinkMind, Digital library)
- 森慎太郎, “コンテンツ指向型無線センサネットワークにおけるオーバヒアリング現象に基づくオフパスキャッシング手法,”電子情報通信学会 ソサイエティ大会 2017, 東京, Sept. 2017.
- 森慎太郎, “コンテンツ指向型無線センサネットワークにおける効率的なキャッシング手法に関する一検討,” 電子情報通信学会 知的環境とセンサネットワーク(ASN)研究会 技術報告, vol. 117, no. 134, pp. 49–52, 札幌, July 2017.
- Shintaro Mori, “Cross-layer design for caching scheme by using successive interference cancellation in information-centric network-based wireless sensor network,” International Journal on Advances in Networks and Services, vol. 10, no. 3&4, pp. 142–151, Dec. 2017. (ThinkMind, Digital library)
- Shintaro Mori, “Fundamental analysis for blockchain-based secured caching scheme for information-centric network-based wireless sensor network,” Proc. 2018 RISP International Workshop on Nonlinear Circuits, Communications, and Signal Processing (NCSP 2018), pp. 517–520, Honolulu, USA, Mar. 2018.
- Shintaro Mori, “Secured caching scheme by using blockchain for information-centric network-based wireless sensor network,” Journal on Signal Processing, vol. 22, no. 3, pp. 97–108, May 2018, doi: 10.2299/jsp.22.97. (J-Stage, Digital library)