A study on secure caching scheme for information-centric wireless sensor networks
Agenda
- Ⅰ. Introduction
- Ⅱ. Related Work and Positioning of This Study
- Ⅲ. Research and Development Items
- Ⅲ.A. Management of cashing data using blockchain-based ledger
- Ⅲ.B. Incentives for nodes that contributed to consensus agreement (introduction of closed-network private bitcoins)
- Ⅲ.C. Definition of behavior when an event occurs (contract definition based on smart contracts)
- Ⅳ. Findings and Results
- Ⅳ.A. Secure caching scheme
- Ⅳ.B. Improvement of block verification
- Ⅳ.C. Device development and evaluationn
- Ⅳ.D. Investigation of communication technology
- Ⅳ.E. Wireless network protocols supporting ICWSN with network coding and constructive interference
- Ⅳ.F. Green ICWSN
- Ⅴ. Conclusion
- Acknowledgement
- Outcomes
Ⅰ. Introduction
Recently, the Internet of Things (IoT) has been deployed in various fields, such as smart homes, security systems, and healthcare, and has become deeply related to our daily lives. Therefore, the sensing data to be collected contains sensitive personal information, and the transmission and retransmission of the data must be efficient and secure. In current IoT-supported systems, when a sensor node (SN), e.g., wearable and individual sensor, accesses a cloud server, the wireless sensor network (WSN) and the Internet are mediated via a gateway. The gateway can generally be selectable for high-performance hardware devices since it does not have a large deployment of inexpensive, non-powerful nodes compared to SNs. In other words, considering a three-tier model of SNs, gateways, and cloud servers, the gateway can be actively involved in selecting, processing, and other information processing, which is a concept like edge computing. Therefore, the system can economize on finite network and frequency resources and effectively process the huge amount of traffic in the future.
In this situation, it is no longer a problem where the data is obtained from but rather what data is to be obtained. Information-centric networking (ICN) technology has been investigated as a next-generation Internet architecture. The current area of applicability is the part of the core network that consists of the Internet. However, the concept of ICN should be extended to wireless networks at the end of the IoT (last mile) to achieve a consistent network architecture. ICN should be introduced into WSNs to achieve a comprehensive network framework, which yields information-centric wireless sensor networks (ICWSNs). ICWSN can provide location-independent data collection and distribution mechanisms, i.e., it has a significant advantage in mobile environments.
In the near future, 5G wireless communication services will be provided, IoT will be a more and more part of daily life, and the demand for security management will be increased. It is already clear that in current society, people's interest is shifting from “end-to-end” to “content” when accessing the Internet via smartphones and other mobile devices toward mature and common services, such as Google, Facebook, Amazon, etc. Therefore, the existing host-oriented network based on IP networks should be replaced with an information-centric architecture, which is inevitable. There is no exception to this trend for wireless networks. As we imagined such a future vision, we found that it was not enough to simply introduce a secure framework. Motivated by the aforementioned background, we focus on a secure caching scheme using blockchain as the first step in ICWSN-framework development.
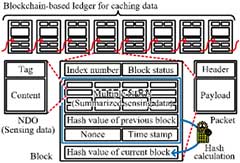
Considering the aforementioned situation, the main goal of this study is to develop a framework that enables secure data cache management when introducing ICN for WSNs. Although other studies focus on efficient methods for caching data, this study investigates the question of how to handle caching data securely, in addition to the efficiency aspect. Therefore, blockchain-based distributed ledgers can be introduced as a management method for caching data, which can respond to attacks by third parties to rewrite (contaminate) cache data. The motivation for blockchain adoption is that it can be organized to be as autonomous, decentralized, and scalable as WSNs. In particular, utilizing the blockchain consensus algorithm, the WSN can be used even if the SNs do not have mutual trust among the SNs, which can provide mutual verification without centralized management.
Ⅱ. Related Work and Positioning of This Study
The survey paper summarized to introduce ICN into future WSNs as the same perspective of this study. For example, there are methods that have been introduced into base stations in cellular networks with virtualization. The same situation applies to DONA (data-oriented network architecture) and NDN (named data networking). As with other research trends, there are user-cooperative caching methods, data selection methods for caching, and dynamic caching methods for video streaming delivery with guaranteed service quality. As far as we know, there have been few previous studies on the use of blockchain to realize secure ICWSNs, which is the reason for its originality and challenge. On the other hand, the results of this study enable the identification of findings and questions for further studies.
Ⅲ. Research and Development Items
As mentioned above, the main goal of this study is to develop a framework that allows the secure management of cached data when introducing ICN for WSNs. To achieve these goals, there are three items of information that need to be recorded on the blockchain: caching data, incentives for nodes that contribute to consensus building, and definitions of actions to be taken when events occur based on sensing data. For these three items, we have set up a scenario for using the functions that can be achieved with blockchain in WSNs in order to solve these problems.
Ⅲ.A. Management of cashing data using blockchain-based ledger
In ICN, the data is represented by units known as name-data objects instead of packets in IP networks. The main difference between named data and packet is that the header of named data only contains information about the type and properties of the content and does not contain addresses. Therefore, those messages regarding data requests in ICN include what kind of data the data requester wants, and the nodes receive the request to verify it matches. In previous studies, the fundamental characteristics of such network systems were evaluated through protocol design, computer simulation-based evaluation, and demonstration using partially testbeds. In this study, based on the findings of the previous study, we will conduct a testbed development, identify and solve the problems related to implementation, and demonstrate the proposed scheme.
Ⅲ.B. Incentives for nodes that contributed to consensus agreement (introduction of closed-network private bitcoins)
In order to maintain a blockchain-based ledger, it is necessary to undertake a mining process in which the nodes mutually verify their data. There are several consensus algorithms for mining, but they all require computing resources on computers. In previous studies, the design assumed that all nodes would cooperate without charge (volunteer) in the mining process for simplicity. On the other hand, considering the practical situation, there should be a mechanism to provide incentives by exchanging incentive fees. Therefore, this study considers introducing blockchain as the framework that underpins the incentive.
Ⅲ.C. Definition of behavior when an event occurs (contract definition based on smart contracts)
As we overview the scheme of future WSNs, the sensing data collected from sensor nodes should not only be aggregated in the cloud but also be utilized by actuators and robots to take actions based on the sensing data. For example, in healthcare, data collected by wearables can be used to observe users' health conditions, in-home networks to detect fires, in smart buildings to detect intruders, and so on. When such an event occurs, it is necessary not only to make an emergency call but also to take actions such as initial movements by the actuators and robots. We will implement this event-action contract information in a framework that uses blockchain as a smart contract.
Ⅳ. Findings and Results
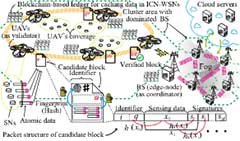


In this study, we focus on the introduction to WSNs of a location (address)-independent network architecture. The goal is to introduce the concept of mutual verification using a distributed ledger based on the blockchain. To achieve this, we establish a scenario in which the functionality that the blockchain can realize is applied to WSNs to solve these problems. Specifically, we perform fundamental and initial evaluations using protocol design, computer simulation, and a simplified testbed. Therefore, we identify the issues that emerge from the introduction of blockchain into WSNs and provide clues for resolving these issues.
Ⅳ.A. Secure caching scheme
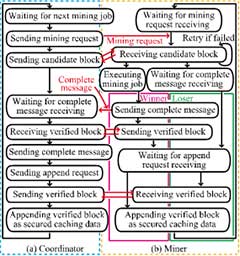
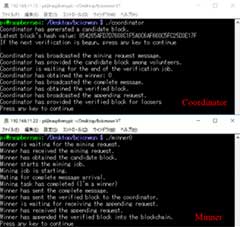
Off-path caching schemes can increase the number of cached nodes, but they cause secured data to be scattered unnecessarily. In light of its friendliness to the ICWSN, which was designed as an autonomous distributed network, we attempted to introduce a distributed ledger based on blockchain. Since blockchain enables mutual verification without any centralized coordination, it can be constructed to be autonomous, decentralized, and scalable. The consensus algorithm can work without any trust among nodes. It is suitable for ICWSN because it can be autonomous, distributed, and scalable, and the consensus algorithm can be established even if the constituent nodes do not trust each other. Since blockchain allows mutual verification without centralized control, we, therefore, proposed a method that can deal with cache data rewriting (cache pollution) attacks by third parties among secure caching methods. The scheme was evaluated using computer simulations and a prototype device (Figs. 1–3).
Ⅳ.B. Improvement of block verification
The consensus method of blockchain used in the previous section is the Proof-of-Work (PoW) method used in Bitcoin and alternative typical cryptocurrencies. In other words, new blocks are committed based on mining among the members who share the blockchain. However, the block verification process requires many calculations (brute force calculations to obtain a specific hash value). It is not suitable for devices that constitute WSNs and have hardware limitations. Therefore, there are issues in terms of its feasibility.
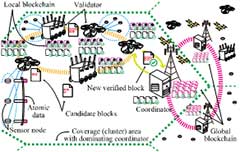
Therefore, we proposed a new voting-based block verification method. The novelty of the proposed method is that it determines which blocks to add to the blockchain by the approval of most of the validation nodes, which we call validators. In addition, UAVs are notable not only for their role as data collectors but also for their work as validators. Block verification is available during the ad hoc wireless transmission between UAVs. Also, it has the advantage of not requiring an exchange mechanism for the transaction fees required for block verification, corresponding to Bitcoin's rewards or Ethereum's gas. A block signature method based on a hash chain for blocks and a protocol design were also studied. Another reason for the breakthrough of this method is that it is not necessary to rely on the design assumed in the initial plan for this study.
Ⅳ.C. Device development and evaluation
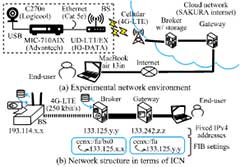
Prior to the demonstration and evaluation in the actual field, a test device was implemented using Raspberry Pi 4 (Quad-core CPU (ARMv8), 8GB RAM, Raspbian (buster) OS). The prototype was a Raspberry Pi 4 combined with 4GPi for LTE connectivity, and the ICN platform was Cefore, an ICN/CCN-based open-source software. In Cefore, daemon processes called cefnetd and csmgrd provide packet forwarding functions for the former and caching functions for the latter. Assuming image data as sensing data, a webcam (Logitech C270n) connected to the main unit via USB 3.0 and controlled by OpenCV was used to capture images, and the image files were saved to local storage and committed to Cefore using the cefputfile command, which was implemented in Python. A processing program was periodically executed every minute using cron. The data submitted by the cefputfile command was cached in RAM on the testbed by the csmgrd daemon process. The cached data after 300 seconds were deleted according to the FIFO algorithm.
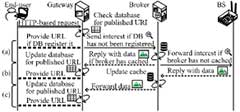
Through long-term operational testing of this prototype device in the laboratory, it was found that issues remained regarding stable operation over long durations. Specifically, the network was suddenly disconnected during continuous operation, scheduled runs suddenly stopped working, and the unit stopped during remote access from an external network. To solve this problem, we replaced the computer with Advantech's MIC-710 AIX (Dual-core CPU (ARMv8.2), 8GB RAM, Ubuntu 18.04 with Jet Pack OS), which has a well-established performance for industrial use (Fig. 6). The MIC-710 AIX platform is designed using the NVIDIA Jetson Xavier NX, which has the advantage that environments implemented on previous prototypes can be easily migrated. Regarding compatibility with existing protocols, a mechanism was implemented for the gateway to exchange sensing data and control messages between the end user and broker in case the user does not support ICWSN protocols. Figure 7 shows the procedure between HTTP/ICN, which is implemented in this paper as a Common Gateway Interface (CGI) on the gateway using the Perl language.
Figure 8(a) shows the network constructed to demonstrate the proposed scheme. In addition, as shown in Fig. 8(b), the broker and gateway were configured with a forwarding interest base (FIB), and the base station (BS) and broker were equipped with cache functions. In particular, it is shown that providing the broker with a cache function reduces data transmission in the radio section, which is a bottleneck section in the system, for the second and later data acquisitions, thereby enabling stable content acquisition through the provision of cached data. Latency (ping values) were 82.9 ms (BS–broker), 0.399 ms (broker–gateway), and 44 ms (gateway–end user). Figure 9 shows the results of access via a program that provides a mechanism to ensure compatibility in terminals that do not support ICWSN. The results show that the desired operation has been achieved.
Ⅳ.D. Investigation of communication technology
Assuming that the proposed ICWSN will be deployed in disaster-resistant smart cities, we investigated the lower layer protocols. In the media access control (MAC) layer, we fundamentally evaluated multi-frame segmentation of upper-layer packets, aiming to recover the original packet even if not all subframes are present using erasure-correction-coded subframes. The proposed scheme can reduce retransmission procedures by retrieving the lost subframes from the neighboring node. In addition, to overcome the channel capacity, we considered using cooperative communication and dual-band-enabled nodes. Computer simulation results show that the system can achieve the scenario in which many nodes are scattered, an environment that was assumed to be unfeasible for conventional wireless communication systems. To evaluate the applicability of ICWSN to the image capture for a river monitoring system as an actual solution for a disaster-resistant smart city, we modified and verified the performance based on the testbed.
Ⅳ.E. Wireless network protocols supporting ICWSN with network coding and constructive interference
In the lower layers of ICWSN, wireless data transmission is based on flooding (broadcast). Therefore, it is necessary to develop new wireless communication technologies, such as lower-layer protocols, compatible with ICN-based network protocols. In the proposed scheme, we investigated MAC and physical layer technologies that support ICWSN based on cooperative communication. The proposed scheme aims to improve transmission efficiency using a network coding (NC) method, aiming at the effect of path diversity due to duplicate transmissions with relay nodes. The key concept of the scheme is to reduce interference based on the phenomenon of constructive interference in relay transmission in which an assisting node intervenes in the relay node and in packet collisions that occur around the relay node. In a typical WSN, the active inter-terminal synchronization and collision avoidance mechanism can be simplified for the sake of device simplicity. The effect of NC data interference in a particular area can be ignored if the receiver node can detect the superposition of the baseband signals from multiple transmitting nodes. In this case, the interference can be ignored. The receiver can detect the correct signal with a higher probability by overlaying multiple carrier signals that are shifted within an acceptable tolerance range. This technique is particularly effective for flooding communications in ICWSN and has been incorporated to achieve packet transmission without serious collisions.
Ⅳ.F. Green ICWSN
The secondary benefit of introducing this study is the greening of the system. In ICWSN, the characteristics include using named data rather than addresses for individual data and caching technology to reduce data transfer and transmission delays. Therefore, it is obvious that the forwarding and receiving of data in the ICWSN can reduce overall system energy consumption by reducing the data transmission distance (caching design) and unnecessary data transmission (pull-type network design). In addition, it is also achievable to make effective use of radio spectrum by reducing the amount of wireless data transmission. However, it is difficult to directly adapt technologies designed for wired networks to ICWSNs because of battery limitations, hardware resource limitations such as computing resources, and a poor wireless communication environment compared to wired networks. Therefore, it is necessary to solve the technical issues that remain to be solved. Consequently, through this research project, we have obtained the findings mentioned in this section.
Ⅴ. Conclusion
This study investigates a blockchain-based secure data caching scheme for information-centric wireless sensor networks, known as post-Internet technology. The proposed scheme is applicable to resource-limited node devices thanks to a novel voting-based verification method. The effectiveness of the scheme was demonstrated based on both computer simulations and hardware-based experiments.
Acknowledgement
A part of this work was supported by JSPS KAKENHI Grant Number JP19K20261.
Outcomes
- 森慎太郎, “コンテンツ指向型無線センサネットワークにおけるセキュアキャッシング手法に対するテストベッドの試作と基礎評価,” 信学技報 SeMI研究会, vol. 119, no. 110, pp. 203–206, Osaka, Japan, July 2019.
- S. Mori, “(Invited) Secure and Effective Caching Scheme using Blockchain for Information-centric Wireless Sensor Networks,” Proc. Asia Pacific Society for Computing and Information Technology (APSCIT) 2019 Annual Meeting, 1 page, Sapporo, Japan, July 2019.
- 森慎太郎, “(依頼講演) コンテンツ指向型センサネットワークにおける高効率・セキュアキャッシング手法の研究,” 信学技報 SeMI研究会, vol. 119, no. 266, pp. 51–53, Tokyo, Japan, Nov. 2019.
- S. Mori, “Caching Data Protection Scheme for Information-Centric Wireless Sensor Networks,” Proc. IARIA the 19th Int. Conf. Networks (ICN 2020), pp. 50–54, Lisbon, Portugal, Feb. 2020.
- S. Mori, “A Fundamental Analysis of Caching Data Protection Scheme using Light-weight Blockchain and Hashchain for Information-centric WSNs,” Proc. 2nd Conf. Blockchain Research & Applications for Innovative Networks and Services (BRAINS 2020), pp. 200–201, Paris, France, Sept. 2020.
- S. Mori, “Secure Caching Scheme using Blockchain for Unmanned Aerial Vehicle-assisted Information-Centric Wireless Sensor Networks,” J. Signal Process., vol. 26, no. 1, pp. 21–31, Jan. 2022.
- S. Mori, “Data Collection Scheme using Erasure Code and Cooperative Communication for Deployment of Smart Cities in Information-centric Wireless Sensor Networks,” Int. J. Advances in Networks and Services, vol. 14, no. 3&4, pp. 54–64, Dec. 2021.
- S. Mori, “Prototype Development of River Velocimetry using Visual Particle Image Velocimetry for Smart Cities and Disaster Area Networks,” Proc. 20th Int. Sympo. Commun. and Info. Tech. (ISCIT 2021), pp. 169–171, Tottori, Japan, Oct. 2021. [DOI][IEEE Xplore]
- S. Mori, “A Fundamental Analysis of an Erase Code-enabled Data Caching Scheme for Future UAV-IC-WSNs,” Proc. IARIA the 20th Int. Conf. Networks (ICN 2021), pp. 8–12, Porto, Portugal, Apr. 2021.
- S. Mori, as a panelist in “P1: Communications beyond the Thinking (spatial, terrestrial, speed, 5G/6G, streaming, high data processing, protocols, etc.),” and entitled “Survey on unmanned aerial vehicle-assisted information-centric wireless sensor networks for smart city applications,” Proc. IARIA the 20 th Int. Conf. Networks (ICN 2021), Porto, Portugal (Hybrid), Apr. 2021.
- 森慎太郎, “情報指向無線センサネットワークにおいてブロックチェーンを用いてセキュアキャッシングを実現するための一検討,” 信学技報 SeMI研究会, vol. 121, no. 105, pp. 35–38, Online, July 2021.
- 森慎太郎, “(チュートリアル) 情報指向無線センサネットワークに関する一研究,” 信学総大 2022, 4 pages, Online, Mar. 2022.
- S. Mori, “A Cooperative and Coded Communication Scheme using Network Coding and Constructive Interference for Information-Centric Wireless Sensor Networks,” Int. J. Advances in Networks and Services, vol. 15, no. 3&4, pp. 54–61, Dec. 2022.
- 森慎太郎, “情報指向無線センサネットワークのテストベッド試作と基礎評価,” 信学技報 SeMI研究会, vol. 122, no. 108, pp. 70–73, Kanazawa, Japan, July 2022.
- 森慎太郎, “(チュートリアル) グリーン情報指向無線センサネットワーク実現のための高効率・省電力化に関する一検討,” 信学総大 2023, 2 pages, Saitama, Japan, Mar. 2022.
- S. Mori, “(Keynote) Information-Centric Wireless Sensor Network: A Study and a Survey,” Proc. IARIA Congress 2022, Nice, France, July 2022. (non peer-review)
- S. Mori, “A Study on Zero-touch-design Information-centric Wireless Sensor Networks,” Proc. IARIA the 22th Int. Conf. Networks (ICN 2023), pp. 7–9, Venice, Italy, Apr. 2023. [Thinkmind (online)] (Best paper award)